| Subject: | Verification of identity |
| From: | Apple-Store@support.com |
| Date: | 2018-04-23 |
| To: | your@email.address |
| X-PHP-Script: | 173.212.240.54/~gagsar/mail111.php for 205.204.85.58 |
| X-PHP-Originating-Script: | 1001:mail111.php |
| X-Source-Args: | /opt/cpanel/ea-php56/root/usr/bin/php-cgi /home/gagsar/public_html/mail111.php |
| X-Source-Dir: | gagsar.safsa:/public_html |
| X-Mailer: | PHP/5.6.35 |
| X-Get-Message-Sender-Via: | vmi177614.contaboserver.net: authenticated_id: gagsar/only user confirmed/virtual account not confirmed |
| X-Mailer: | PHP/5.6.35 |

Scam alert! The E-mail above is a SCAM. It’s a Phishing scam, pretending to be from the Apple Store. Trying to get your Apple account-details by luring you to a fake Apple website. The message is all fake. The real Apple did NOT send this. Be warned!
If you’ve more information and/or received this message too please comment below. Describe how you got it (as an e-mail or comment?, the message etc), thanks in advance! Then mark it as SPAM (if possible) and/or DELETE it.
Analysing this phishing mail
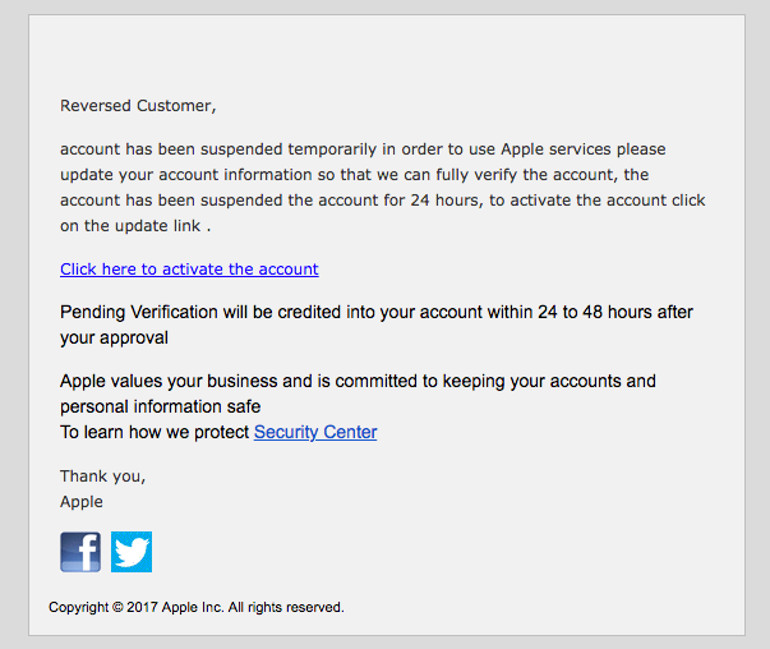
The message in text:
Reversed Customer,
account has been suspended temporarily in order to use Apple services please update your account information so that we can fully verify the account, the account has been suspended the account for 24 hours, to activate the account click on the update link .
Click here to activate the account
Pending Verification will be credited into your account within 24 to 48 hours after your approval
Apple values your business and is committed to keeping your accounts and personal information safe
To learn how we protect Security Center
Thank you,
Apple
Copyright © 2017 Apple Inc. All rights reserved.
The email links have been disabled for your safety, but they lead to the following webpages:
http://149.56.141.163/~fwafwawf/Help.php [Click here to activate the account]
http://5.56.61.7/~aawwwwaa/up.php [Security center]
The latter doesn’t do much but the first leads to a redirect script. It’s hosted on 163.ip-149-56-141.net owned by the hosting-provider OVH SAS (AS16276). It redirects to:
http://finelgmas.com/cgi-bin.appIe-update-information/#!&page=signin
Now we get the following fake Apple website:

The site may look real until you notice (besides the web-address not being "apple.com") none of the links actually work and the site isn’t protected with SSL encryption (https: instead of http:).
After entering fake account-details we’ll see a spinning wheel for a few seconds and then the same screen but the login-form is gone… That’s it. They have stored your account details and don’t bother redirecting you anywhere.
The domainname ‘finelgmas.com’ is hosted on vmi174081.contaboserver.net (173.249.27.44) by a German hosting company called Contabo GmbH. The domain is registered at Internet.bs located in the Bahamas. It offers free domain privacy service which is probably the reason why the scammers registered this domainname here.
Domain Name: FINELGMAS.COM Registry Domain ID: 2255858609_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.internet.bs Registrar URL: http://www.internet.bs Updated Date: 2018-04-23T11:59:49Z Creation Date: 2018-04-23T11:59:48Z Registry Expiry Date: 2019-04-23T11:59:48Z Registrar: Internet Domain Service BS Corp Registrar IANA ID: 2487 Registrar Abuse Contact Email: Registrar Abuse Contact Phone: Domain Status: clientTransferProhibited Name Server: NS1.CONTABO.NET Name Server: NS2.CONTABO.NET Name Server: NS3.CONTABO.NET DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
Even worse.. the whois-service referred to doesn’t work so we can’t find any further details about the registrant. Probably enough to submit a whois inaccuracy complaint to ICANN!


