We’ve seen Paypal being the target for phishing scams before. This time in French, targeting French speaking Paypal users:
| Subject: | Activité récente inhabituelle |
| From: | Service Restriction <Support-wallet@loanditer.be> |
| Date: | 2018-04-15 |
| To: | your@email.address |
![]()
Activité de connexion inhabituelle
Nous avons trouvé une connexion inhabituelle avec le compte PayPal sur une connexion récente, une étape de sécurité supplémentaire est requise.
Pays / Région: California, US
Adresse IP: 213.174.123.194
Date: 15/04/2018 06:43
Veuillez suivre les étapes pour retrouver un plein accès a votre compte.
Se connecter
Se connecter
Copyright © 1999-2018 PayPal. Tous droits réservés.

Scam alert! The E-mail above is a SCAM. It’s a Phishing scam, translated into French. Trying to get your bank-details by luring you to a fake bank website. The message is all fake. The real PayPal did NOT send this. Be warned!
If you’ve received this by e-mail than forward it to the Paypal fraud team. After that mark it as SPAM (if possible) and/or DELETE it.
Analysing this phishing mail
The message is very much like previous Paypal phishing Emails but in French. It translates to:
![]()
Unusual connection activity
We found an unusual connection with the PayPal account on a recent connection, an extra security step is required.
Country / Region: California, US
IP address: 213.174.123.194
Date: 15/04/2018 06:43
Please follow the steps to regain full access to your account.
Login
Login
Copyright © 1999-2018 PayPal. All rights reserved.
The mentioned IP-address is actually not from California, US but from Paris, France. But well.. the story is fake anyway.
IP-address: 213.174.123.194 GeoIP Country Edition: FR, France GeoIP City Edition, Rev 1: FR, A8, Ile-de-France, Paris, 75001, 48.862801, 2.329200, 0, 0 GeoIP ASNum Edition: AS29283 Hub One SA
Tracing the links in this phishing e-mail
The LOGIN-link in this e-mail points to a bit.ly URL-shortener link. (For your safety these links have been removed above!) You can check the bit.ly statistics for this link.
This URL-shortener redirects to the following URL:
http://www.dangcap9x.vn/wp-admin/user/se_connecter/62XjI/signin.php?country.x=&locale.x=en_
It seems they have used a hacked WordPress site to store a fake Paypal website on it. It shows a webpage with a fake (rather empty) PayPal login-screen:
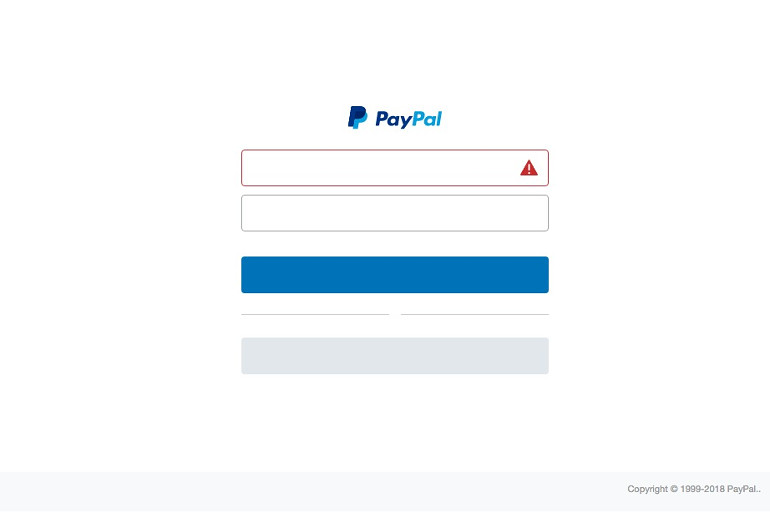
They want you to log in so they have your PayPal username and password. After “logging in” with fake details (test@fake.paypal) the fake Paypal site continues in English. We get the following page:
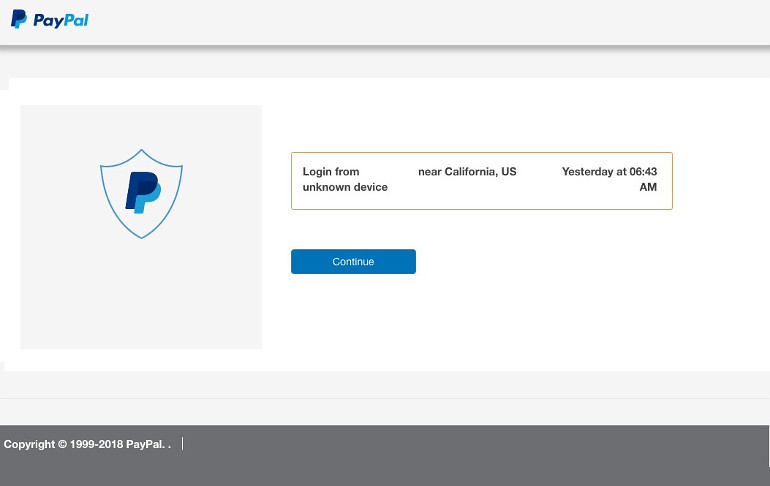
Now they have your Paypal login details to abuse! But they aren’t finished with you… After clicking on [Continue] we get the following page:
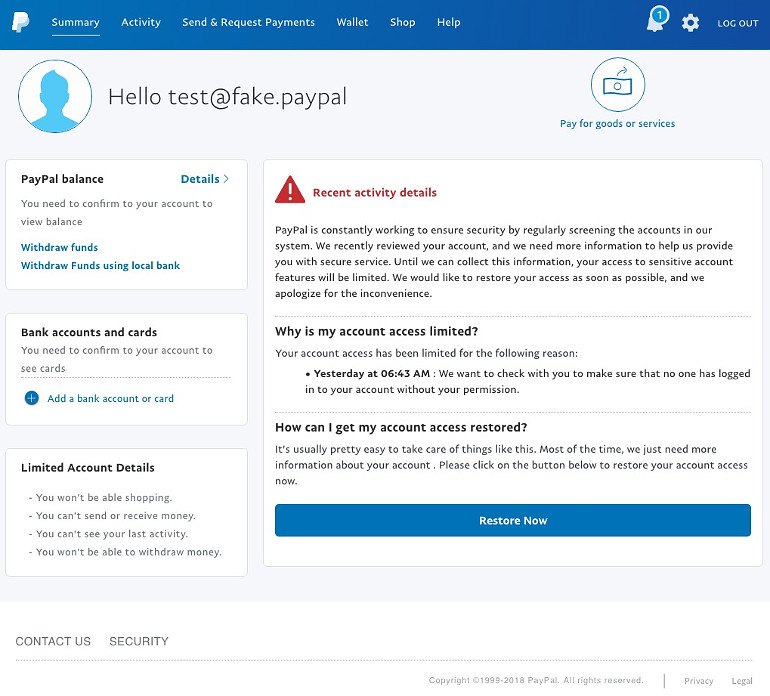
There is definitely much more on the webpage now, but practically no link works. This way they force you to do the only action they want you to do… to click on [Restore Now]! This leads to the following page with a detailed webform:
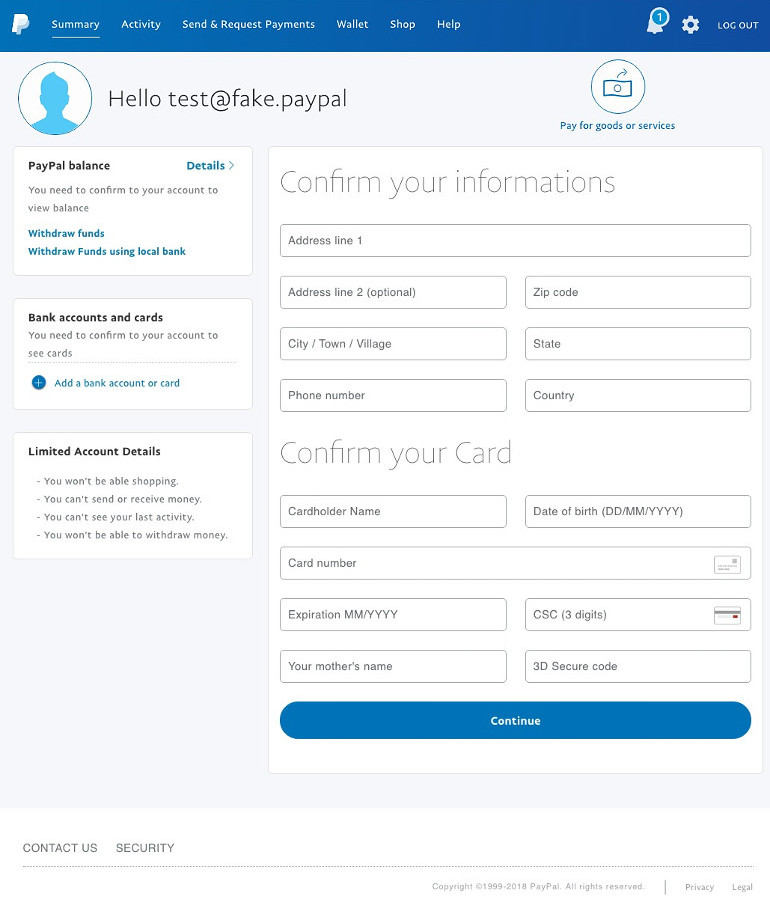
Here they ask you to fill in all your personal and your creditcard details! It actually has a check function to see if the given creditcard is valid! Unbelievable…
After submitting (fake) details they ask us which (regular) bank we use:

Yes.. while the’re at it they want to get as much banking details from you as possible! (Although the choices seem mainly US focussed.) After selecting your bank they have the nerve to ask you to upload an ID card in the next page!
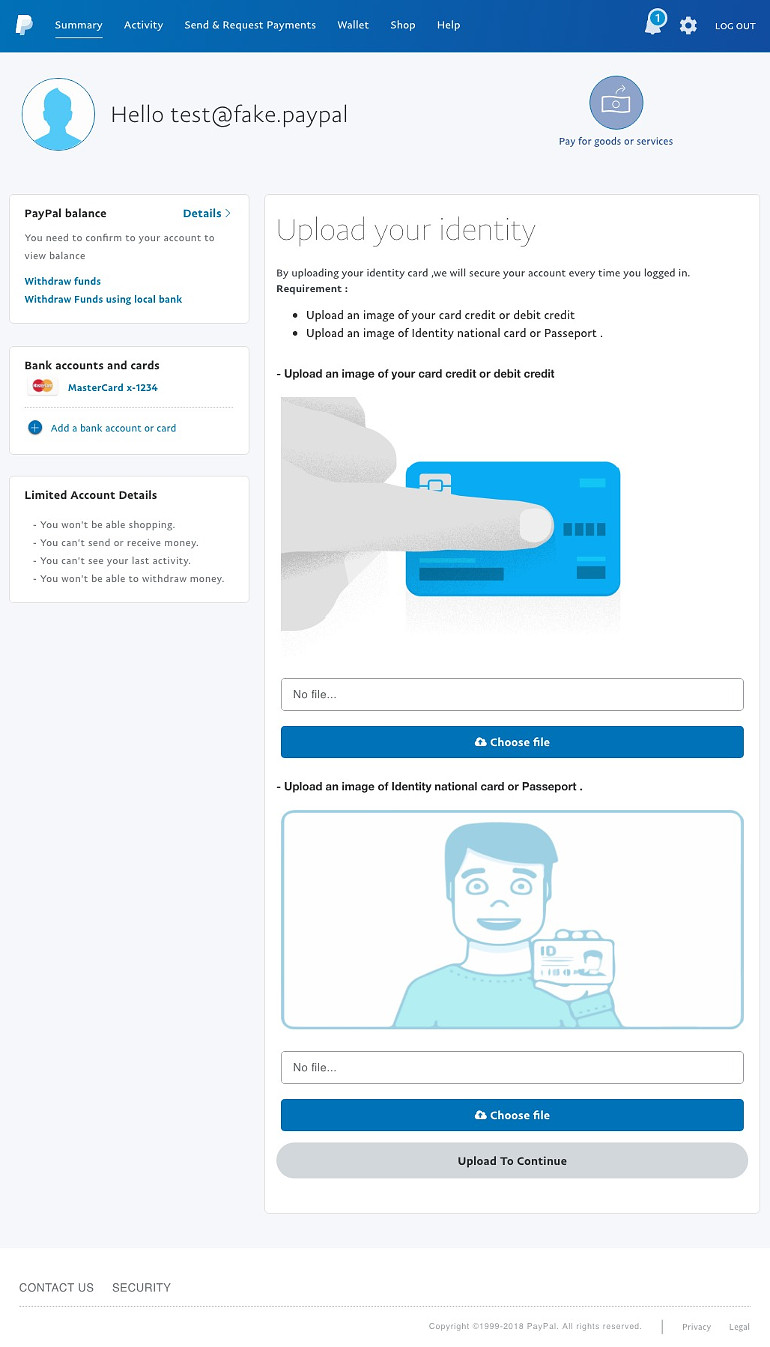
We have provided our ID card to see what else they have in store for us!

But.. they seem very satisfied with us and show us a page that we are ready restoring our account. After all.. they now have your Paypal account, credit card details, banking details, personal details, ID card. They can do a lot of damage with these details!
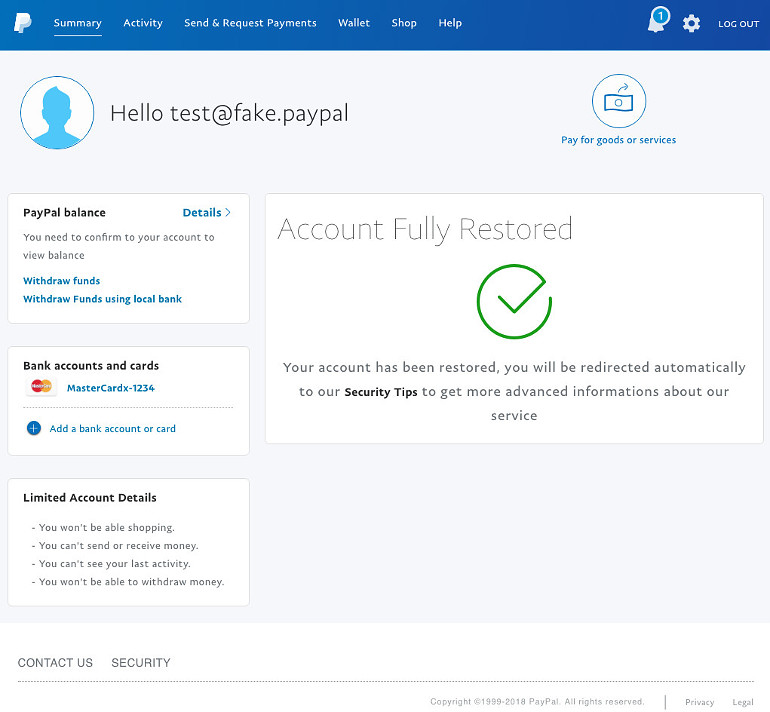
After a few seconds the page redirect you to the real Paypal website, to a security info page of all places!
As stated above, the fake Paypal site seems to be hidden onto a hacked WordPress website from someone in Vietnam.
www.dangcap9x.vn is an alias for dangcap9x.vn. dangcap9x.vn has address 112.213.85.32 dangcap9x.vn mail is handled by 10 dangcap9x.vn. 32.85.213.112.in-addr.arpa domain name pointer mx8532.superdata.vn. GeoIP Country Edition: VN, Vietnam GeoIP City Edition, Rev 1: VN, 67, Tra Vinh, Nguyên, N/A, 9.847800, 106.345596, 0, 0 GeoIP ASNum Edition: AS45544 SUPERDATA
When we check http://www.dangcap9x.vn it actually showed a defaced page from some hacker named "Venganza" (which means Vengeance in Spanish)!
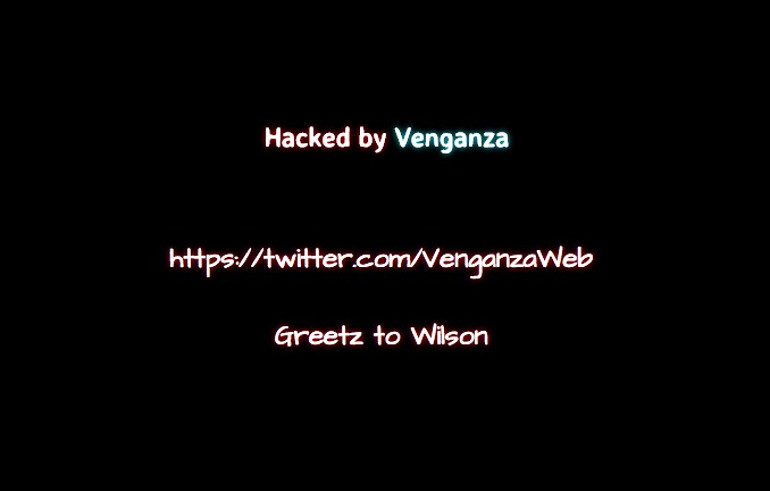
We don’t know if this hacker "Venganza" is also responsible for the Paypal scam or that he sold this hacked site to scammers. The twitter-account mentioned does exist:
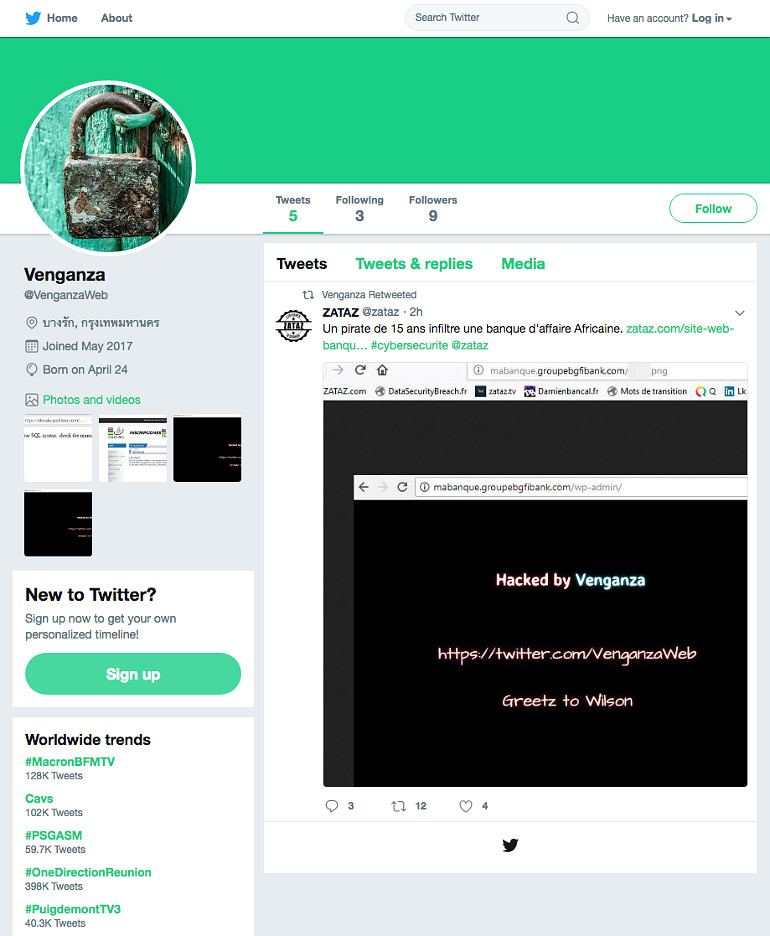
But the only tweet found here is a retweet of an article from Zataz, a French security blog, about A 15-year-old hacker who infiltrates an African business bank. The image displayed is the same deface tag used here. So is this Venganza bragging on his twitter about the bank-hack? Is he the 15-year old hacker mentioned? Who knows… Our investigation ends here.


