| Subject: | Original Bill of Lading – Shipping Documents |
| From: | Maersk Line <shippingdocs@maerskline.com> |
| Date: | Thu, 30 May 2019 |
| To: | your@email.address |

Dear Customer,
Please find attached below your Bill of Lading, Packing List and Invoice for the current shipment headed to your port.
Shipping customer advised us to contact your email (your@email.address) as it was listed as the consignee/receiver of the goods in transit.
Below are the shipping documents:

ETA of cargo also included in the attached files.
Thank you for your continued support.
Best regards,
Maersk Line
The information contained in this message is privileged and intended only for the recipients named.
Any unwanted review, dissemination or copying of this message or the information it contains is prohibited.
If you have received this message in error, please immediately notify the sender, and delete the original message and attachments.
Please consider the environment before printing this email.

Scam alert! The E-mail above is a SCAM. It’s a Phishing scam, the message is fake and spammed to multiple addresses. It was NOT sended by Maersk! The scammers just faked the sender-address. The scammers try to get you to go to their fake Maersk website to acquire your login details.
If you’ve received this by e-mail than mark it as SPAM (if possible) and/or DELETE it. DO NOT enter any details!
First of all, this spammed email is trying to confirm your email address by requesting to be notified by your email client. This will be sended to: takingbox2018@gmail.com If you have auto confirmation setup, you’ll not even notice this has happened.
The sender-address has been forged to make it look like maerskline.com was the original sender. This fails partly because the sending host is not authorized in Maerskline.com’s SPF-record which uses a soft-fail (~all) so the email may still arrive (hopefully in your spambox).
Relevant headers:
Disposition-Notification-To: takingbox2018@gmail.com X-AntiAbuse: This header was added to track abuse, please include it with any abuse report X-AntiAbuse: Primary Hostname - server.goodseedsplantationx.com X-AntiAbuse: Sender Address Domain - maerskline.com X-Get-Message-Sender-Via: server.goodseedsplantationx.com: authenticated_id: field@twicksparade.com X-Authenticated-Sender: server.goodseedsplantationx.com: field@twicksparade.com SPFCheck: Soft Fail, 30 Spam score X-Antivirus-Scanner: Clean mail though you should still use an Antivirus
The email talks about "shipping documents" and has a fake PDF-document thumbnail in the message body. This is just an image, there are no actual attached files in this email.
The only thing you can do is click on the link below the thumbnail image to get you to go to their fake Maersk website (the actual link has been removed in the email above).
The link in the email points to the following Rebrandly URL (a URL shortener) with your email address as a GET-parameter:
https://rebrand.ly/n00tl3/?email=your-email@address.tld
This points to a Ngrok.com URL tunnel to a self hosted website:
https://ceec3091.ngrok.io/oh/bad/BL/download/maersk?email=your-email@address.tld
This loads the phishing website:
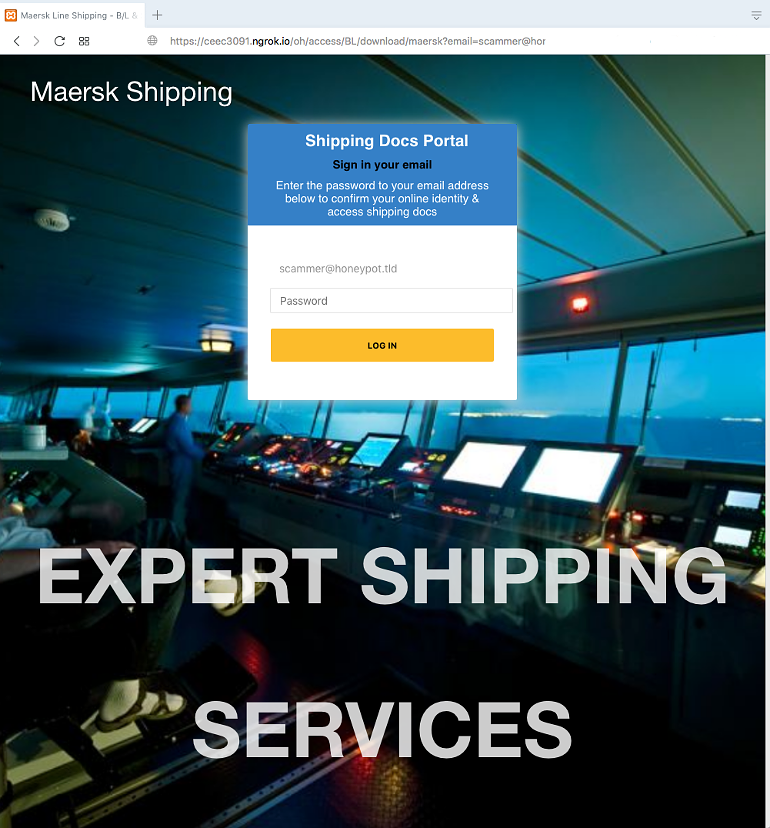
They actually tried to make the page look nice by alternating different background images (photos with Maersk ships & containers). The real Maersk website looks quite different, the real login-page just has a white background. Offcourse the real website displays a menu-bar leading to many more pages. I guess they didn’t want to fake these and also to not distract the visitor from their phishing login-form.
The e-mail has been auto-filled (passed as a GET-param). You can enter a password but whatever you type, the next result is the same page with the message that your login has failed:
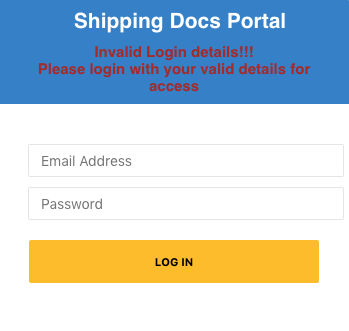
Meanwhile they stored it so they now have your login credentials to abuse.
The Ngrok cloud-service is mostly used by developers to e.g. let clients test their (locally hosted) new website. This system may be set-up by the scammers, or this phishing site is hosted on a hacked system.
It’s a Windows host running XAMPP for Windows 7.1.27. A PHPinfo link could be found in the Xampp dashboard providing details about this system (here provided as a PDF-document).
The mentioned companies have been warned about this abuse.



1 thought on “Maersk Line phishing mail”
Webmaster
(June 7, 2019 - 4:01 pm)Update: It seems that Rebrandly didn’t close this shortlink and/or user account responsible, so when Ngrok did shutdown the URL tunnel to the phishing website the scammers just changed their rebrandly shortlink to point to another tunnel hosted at: 06a52317.ngrok.io/oh/access/BL/download/maersk?email=
So this fake Maersk (phishing) website is still in the air after a week!